Security in Mobile Applications

When developing applications we need to be careful with security.
The Open Web Application Security Project® (OWASP) is a non-profit foundation working to improve software security.
They make a document, called OWASP Top 10, to make developers aware of web application security.
And for the world of mobile applications they also have an equivalent document and there is also a security standards document - the OWASP MASVS (Mobile Application Security Verification Standard) that contains the following categories:
- MASVS-STORAGE: Secure storage of sensitive data on a device (data-at-rest).
- MASVS-CRYPTO: Cryptographic functionality used to protect sensitive data.
- MASVS-AUTH: Authentication and authorization mechanisms used by the mobile app.
- MASVS-NETWORK: Secure network communication between the mobile app and remote endpoints (data-in-transit).
- MASVS-PLATFORM: Secure interaction with the underlying mobile platform and other installed apps.
- MASVS-CODE: Security best practices for data processing and keeping the app up-to-date.
- MASVS-RESILIENCE: Resilience to reverse engineering and tampering attempts.
Okay, but how can we analyze these vulnerabilities in our applications?
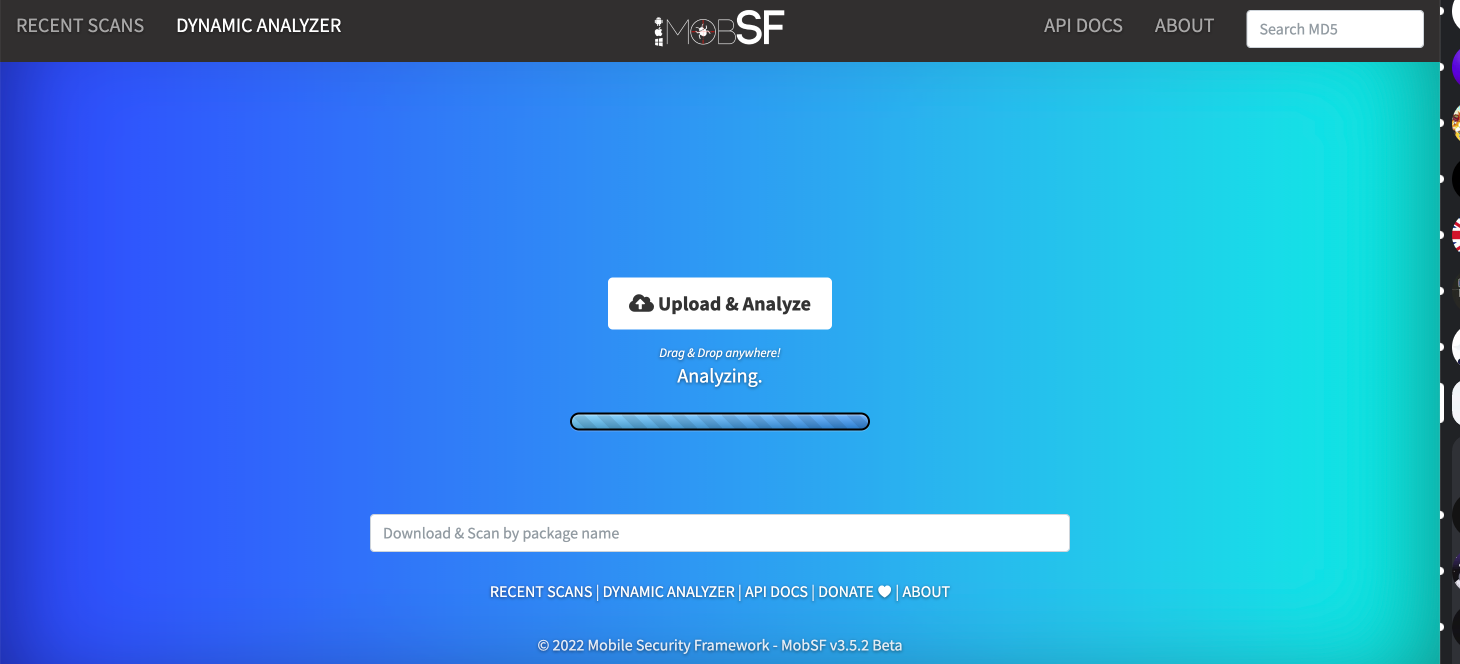
The Mobile Security Framework (MobSF) is a complete automated framework for mobile applications (Android/iOS/Windows) for vulnerability testing, malware analysis and security assessment framework capable of performing static and dynamic analysis.
You can install it on your machine and put the APK or IPA of your applications to run the tests:
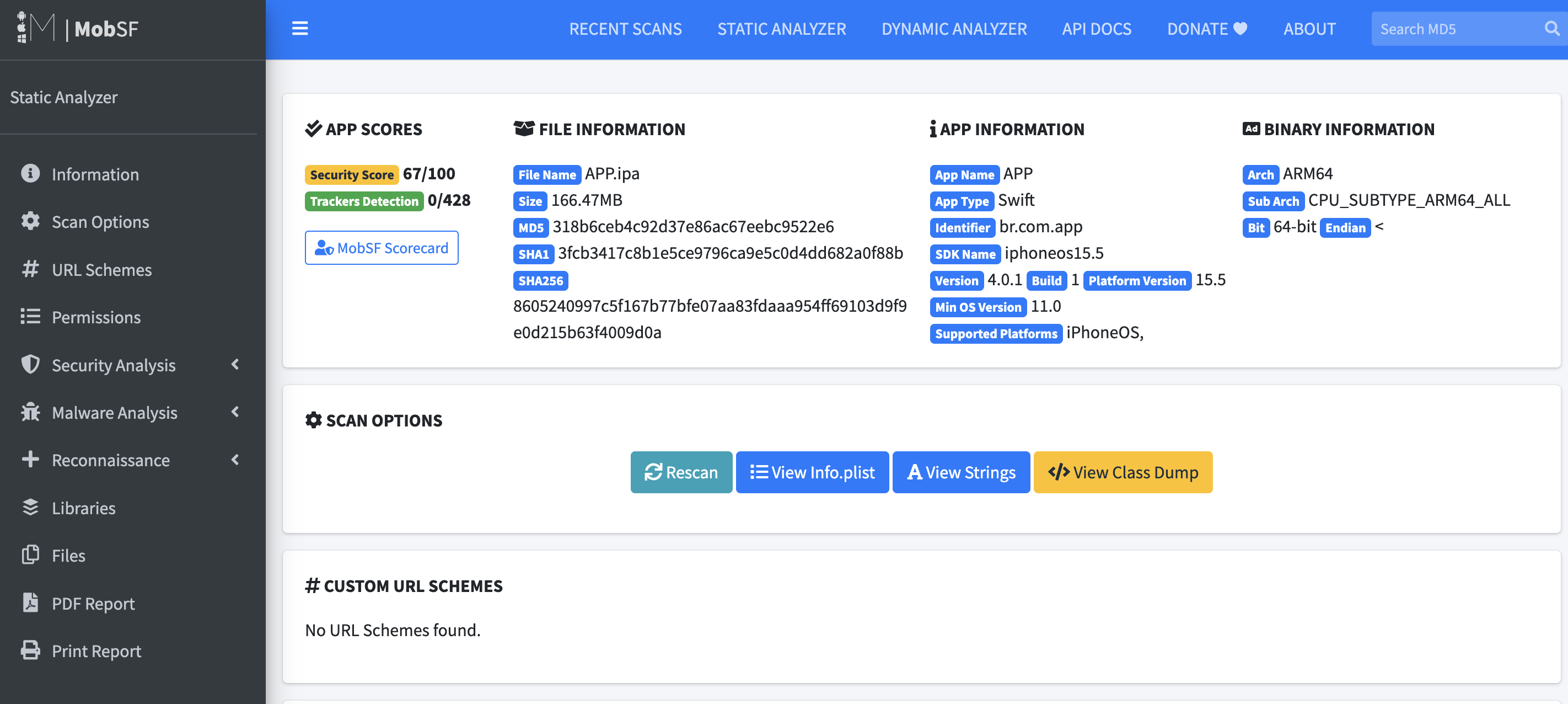
At the end it gives a report with the vulnerabilities:
An important point are credentials that we sometimes leave exposed or test files that are sometimes placed in our applications. For example, in React Native it is possible to exclude some files from our app's bundle:
const exclusionList = require('metro-config/src/defaults/exclusionList');
// exclusionList is a function that takes an array of regexes and combines
// them with the default exclusions to return a single regex.
module.exports = {
solve: {
blacklistRE: exclusionList([/dist\/.*/])
}
};
There is also this dynamic instrumentation toolkit for developers, reverse-engineers, and security researchers called Frida that can help us run security tests.
So developer, keep your app safe.
Embedded content: https://docs.google.com/presentation/d/1jVQCL2h-xKEypVAPo-MU_LGoQS-CsYYXhAC9RNOpJ94/edit?usp=sharing